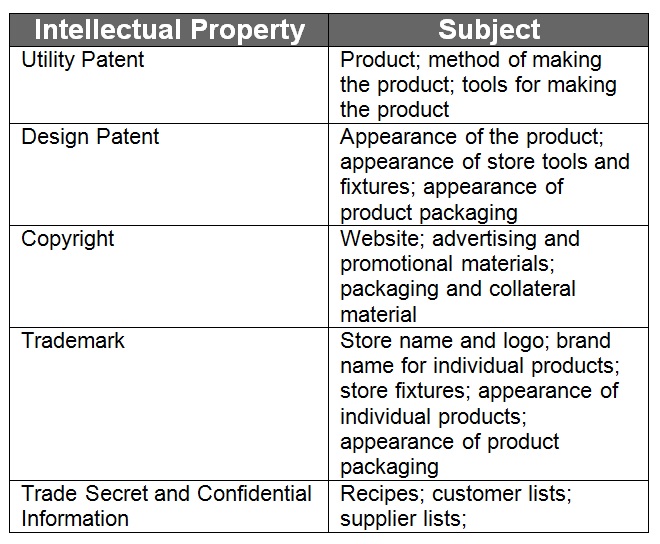
The perfect confidentiality agreements is, in most cases, overkill and in any event probably never would be signed. Hundreds, if not thousands of CDAs, NDAs, and other secrecy agreements are signed every day, and the vast majority perform adequately for their purpose. Rather than chase perfection, the parties should focus on avoiding mistakes.
From the Perspective of the Disclosing Party
Prevent disclosure and use. The disclosing party should make sure that the agreement not only prevents disclosure but also use of the confidential information.
Define protected information. The definition of protected information should include anything that the disclosure is likely to disclose. The disclosing party should resist requirements that could result in accidental forfeiture, such as requirements that the information be marked confidential or that oral disclosures must be confirmed in writing.
Define the time. The duration of the receiving party’s obligations should be clearly defined, as should the period of time during which the disclosing party can disclose information under the agreement.
Have an enforcement plan. If the party to the agreement discloses or uses the information, there is a breach of contract action. However, if a rogue employee or contractor, who is not a party to the agreement, discloses or uses the information, what is the plan? The agreement can provide a right of enforcement, or require the receiving party to enforce the agreement on the disclosing party’s behalf.
Unnecessary obligations. While it is easier to get a reasonable agreement when the provisions are mutual, a disclosing party should not accept confidentiality obligations to the receiving party if it does not need to.
Disclosing Party Options. Ownership. The disclosing party may want to control ownership of inventions inspired by the disclosed invention. Non-filing. The disclosing party may want to restrict the receiving party from filing patent applications on subject matter inspired by the disclosure. No Export. The disclosing party may want to prevent export of the information. Choice of law. The disclosing party may want to select law that will protect the disclosed information. Choice of forum. The disclosing party may want to select a forum that is convenient and reliable, No warranties. The disclosing party may want to disclaim any warranties about the disclosed information. No obligation. The disclosing party may want to disclaim an obligation to deal further with the disclosing party.
From the Perspective of the Receiving Party
Define protected information. The receiving party needs to precisely define the information that is subject to the confidentiality obligations,
Exceptions. The receiving party should define exceptions to its obligations for information that is already in the public domain; information that the receiving party already had in its possession, and information that subsequently comes into its possession other than from a breach of duty to the disclosing party.
Define the time. The receiving party needs to know how long to maintain confidentiality, and how long the disclosing party can make disclosures that the receiving party has to protect.
Receiving Party Options. Confidentiality. The receiving party may want some protection for its own information that it might exchange with the disclosing party. No obligation. The receiving party may want to disclaim an obligation to deal further with the disclosing party. Choice of Law. The receiving party may want to know the law that applies to the construction and enforcement of the agreement. Choice of forum. The receiving party may want to limit where it can be sued to enforce the agreement.
Checklist for a Confidentiality Agreement
- Parties properly identified
- Definition of protected information
- Obligation not to disclose protected information
- Obligation not to use protect information
- Duration of obligation to protect protected information
- Duration of agreement (period of disclosures by disclosing party)
- Indemnity by receiving party for breaches by those to whom it discloses the protected information
- Representations by receiving party
- Ability to enter into agreement
- Agreements with third parties to ensure performance
- Ownership of developments based upon disclosed information.
- Promise not to file filing patent applications on subject matter inspired by the disclosure.
- No Export of the disclosed information.
- Choice of law that applies to the agreement.
- Choice of forum where agreement can be enforced.
- Disclaimer of warranties regarding the disclosed information.
- Disclaimer of obligation to deal further with the other party.
- Boilerplate
- Assignability
- Severability
- Effectiveness of copies
- Integration
- Authority of Signatories